VMware sandbox escape bugs are so critical that patches are being released for end-of-life products
VMware sandbox escape bugs are so critical that patches are being released for end-of-life products
Multiple VMware products are affected - with some of the vulnerabilities scoring a staggering severity rating of 9.3 out of 10.
Published on 8th March 2024
VMware is urging customers to patch critical vulnerabilities that make it possible for hackers to break out of sandbox and hypervisor protections in all versions, including out-of-support ones, of VMware ESXi, Workstation, Fusion, and Cloud Foundation products.
A constellation of four vulnerabilities—two carrying severity ratings of 9.3 out of a possible 10—are serious because they undermine the fundamental purpose of the VMware products, which is to run sensitive operations inside a virtual machine that’s segmented from the host machine. VMware officials said that the prospect of a hypervisor escape warranted an immediate response under the company’s IT Infrastructure Library, a process usually abbreviated as ITIL.
“Emergency change”
“In ITIL terms, this situation qualifies as an emergency change, necessitating prompt action from your organization,” the officials wrote in a post. “However, the appropriate security response varies depending on specific circumstances.”
Among the specific circumstances, one concerns which vulnerable product a customer is using, and another is whether and how it may be positioned behind a firewall. A VMware advisory included the following matrix showing how the vulnerabilities—tracked as CVE-2024-22252, CVE-2024-22253, CVE-2024-22254, CVE-2024-22255—affect each of the vulnerable products:
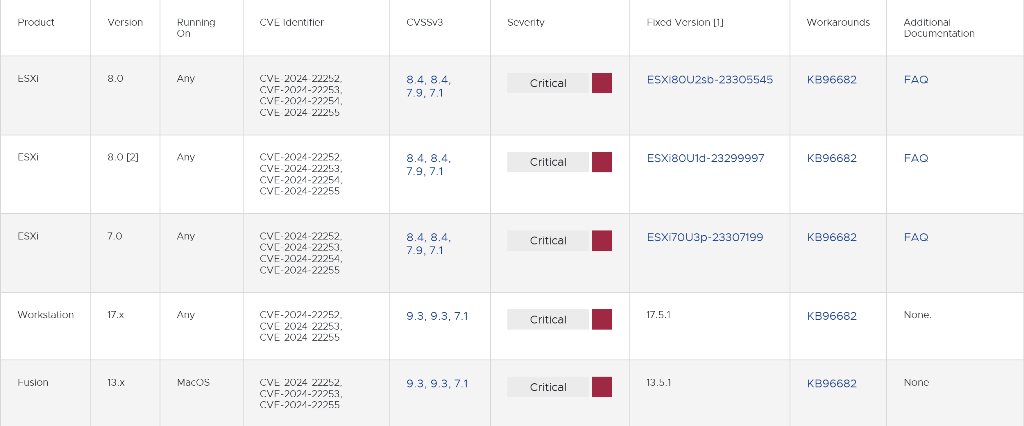
Three of the vulnerabilities affect the USB controller the products use to support peripheral devices such as keyboards and mice. The advisory describes the vulnerabilities as:
CVE-2024-22252: a use-after-free vulnerability in XHCI USB controller with a maximum severity range of 9.3 for Workstation/Fusion and a base score of 8.4 for ESXi. Someone with local administrative privileges on a virtual machine can execute code as the virtual machine’s VMX process running on the host. On ESXi, the exploitation is contained within the VMX sandbox, whereas, on Workstation and Fusion, this could lead to code execution on the machine where Workstation or Fusion is installed.
CVE-2024-22253: a use-after-free vulnerability in UHCI USB controller with a maximum severity rating of 9.3 for Workstation/Fusion and a base score of 8.4 for ESXi. Exploitation requirements and outcomes are the same as for CVE-2024-22252.
CVE-2024-22254: an out-of-bounds write vulnerability with a maximum severity base score of 7.9. This vulnerability makes it possible for someone with privileges within the VMX process to trigger an out-of-bounds write, leading to a sandbox escape.
CVE-2024-22255: an information disclosure vulnerability in the UHCI USB controller with a maximum CVSSv3 base score of 7.1. Someone with administrative access to a virtual machine can exploit it to leak memory from the vmx process.
Broadcom, the VMware parent company, is urging customers to patch vulnerable products. As a workaround, users can remove USB controllers from vulnerable virtual machines, but Broadcom stressed that this measure could degrade virtual console functionality and should be viewed as only a temporary solution. In an article explaining how to remove a USB controller, officials wrote:
The workaround is to remove all USB controllers from the Virtual Machine. As a result, USB passthrough functionality will be unavailable.
In addition, virtual/emulated USB devices, such as VMware virtual USB stick or dongle, will not be available for use by the virtual machine. In contrast, the default keyboard/mouse as input devices are not affected as they are, by default, not connected through USB protocol but have a driver that does software device emulation in the guest OS.
IMPORTANT:
Certain guest operating systems, including Mac OS, do not support using a PS/2 mouse and keyboard. These guest operating systems will be left without a mouse and keyboard without a USB controller.
VMware said it isn’t aware of any evidence that any of the vulnerabilities are under active exploitation.












