The silent security threat: why IT leaders must regain control of their software ecosystem
The silent security threat: why IT leaders must regain control of their software ecosystem
Shadow IT is on the rise, exposing organisations to compliance, security and cost challenges - with a strategic IT asset management approach critical to control these threats.
Published on 5th November 2025
Many organisations are unknowingly exposing themselves to major threats by allowing shadow IT to flourish.
A failure to understand how business units and individual employees are purchasing their own software and installing free applications, as well as continuing to use end of life (EOL) software, could have dire consequences. There are many cautionary tales of IT teams losing control of IT assets and being unable to stop sensitive data from being accessed by unauthorised personnel and shared on unofficial platforms.
Shadow IT can also make an organisation more vulnerable to a cyber attack and result in serious disruptions, affect compliance which leads to fines, and interrupt operations because the application does not integrate properly with a company’s IT infrastructure.
It is critical, therefore, to have an effective IT asset management strategy, and to put governance in place to discover and monitor shadow IT.
Why visibility is crucial
IT leaders need access to reliable data to remove EOL assets that could be highly vulnerable, and to know where they have unpatched apps that pose the biggest threats.
“In a hybrid world, organisations must know what hardware, software, SaaS and cloud inventory they have, where it is installed, who has access to it and how it is being consumed so they can make better business decisions,” says Kevin Miller, director of product marketing at hybrid IT asset management specialists, Flexera.

“It can come down to communication and how people are onboarded and offboarded. What applications are they given and have access to, and what are they installing on premises and accessing via the web?”
It can mean that without a comprehensive view of SaaS applications and other software throughout an organisation, shadow IT can run unchecked and leave an organisation open to security risks, application sprawl and wasted spend.
Often employees will buy and use software that serves the same purpose as that already bought by the organisation and thus increase the company’s security risks and costs. There is also a risk to productivity if multiple tools are doing the same thing and employees are unclear which is the best tool for different work challenges.
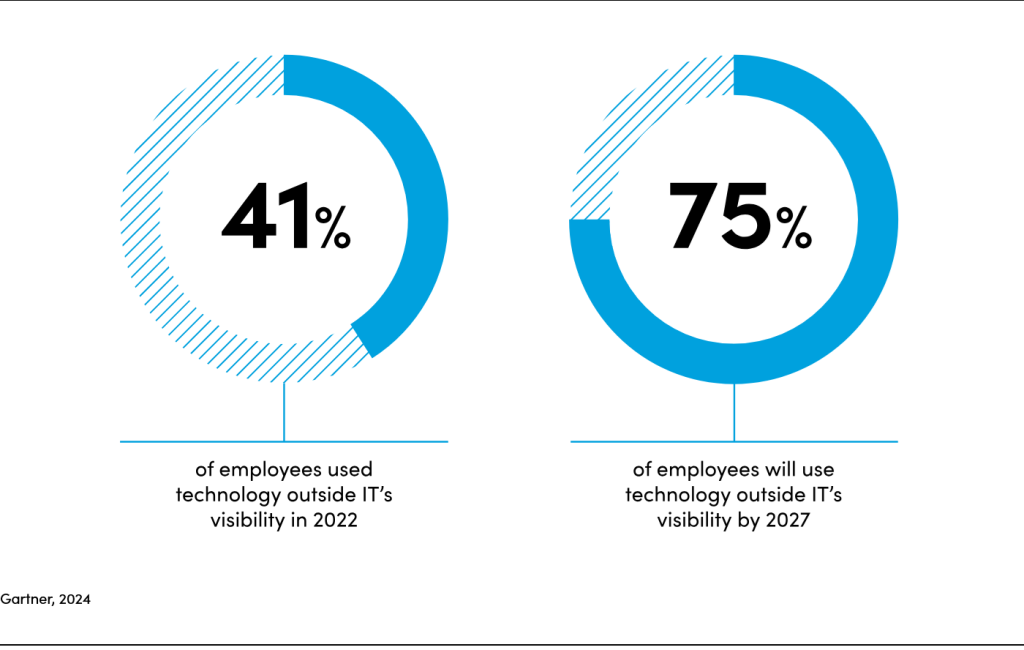
According to Gartner’s Market Guide for SaaS Management Platforms report, IT leaders are typically only aware of one third of the SaaS apps being used. This is partly because people are working in a hybrid way and so the purchasing and governance of IT applications has become decentralised.
Flexera’s own 2025 State of the Cloud report questioned 750 cloud decision-makers and found that cloud resources now comprise 55% of workloads.
“There often are vulnerabilities associated with outdated software, especially when those assets are end of life or support. It’s vital to know how many versions behind your installations are for proactive risk mitigation,” adds Miller. “Organisations typically don’t know where in the business shadow IT is being used and what the critical impact might be if the software was breached.”
Regaining control through governance and collaboration
Organisations are advised to use discovery tools to identify shadow IT across their on-premises, cloud and SaaS environments.
Fellow director of product marketing at Flexera, Jennifer Kuvlesky, urges more real-time visibility and automated governance to plug compliance and security gaps. She says it is too easy for different internal business units to buy IT assets, with employees commonly purchasing products they use for work on credit cards or purchasing applications without checking with IT.
“Organisations must be more proactive from the beginning of the purchasing process when it comes to governance. They must have more visibility around what is going on,” she says. “It is too easy for anyone to buy IT. Policies that state clearly what will be paid for can help, but there must be robust controls and visibility over what applications are being used and by whom.”
“With SaaS and with cloud applications, we are not just talking about installations anymore. There are different licensing and methods of procuring applications, and organisations need help to make sense of everything.”
Her advice to IT leaders is to map the enterprise environment to see which applications are being used on-premises, in the public cloud and on SaaS platforms, in which areas of the business, and to use multiple discovery methods to understand what is going on within an organisation. This is where partners such as Flexera can offer advice and guidance and help organisations see across their entire IT estate..
“Once you know how data is being captured, who is using which applications, the cost and the potential risks, you can begin to implement policies,” she says. “This might include stopping people purchasing pay-as-you-go licences.”
Miller agrees, and says companies need to be more aware of how people are acquiring applications outside of corporate IT processes and policies.
His recommendation is to combine all discovery sources within a centralised source to generate insights.
“This will create a normalised view of your technology data to see, for example, where things might overlap.”
He cites the world of mergers and acquisitions where two or more companies come together, or are being divested, and where there might be overlapping applications across the different organisations.
“We had a recent divestiture example where one company controlled 80% of the business. So which applications stay with that company and which with the smaller company?” says Miller.
“We walked through their technology estates with them to understand the lifecycle of the applications being used to decide which ones to remove, patch-up or migrate between departments. However, you must also share this information with the individual application owners within different business units to update appropriately, which adds another set of stakeholders.”
Indeed, it is important to communicate well, assign accountability and create clear governance policies to reduce future risks. The question is who should take responsibility for making these decisions internally?
Kuvlesky insists that accountability must be shared among the c-suite, including between the CIO, the CEO and CISO because, if there is a security breach, the buck stops with them.
“Governance must be a centralised decision,” she says. “We do not want to stop innovation or stop business units procuring tools that are going to make them more productive. This is about ensuring back-end policies are effective and everyone is aware of them as part of a robust IT asset management strategy.”
Shadow IT isn’t just an inconvenience, it’s a ticking time bomb. Without control and oversight, businesses risk security breaches, spiralling costs and operational chaos.

