Microsoft Teams vulnerability allows attackers to deliver malware to employees
Microsoft Teams vulnerability allows attackers to deliver malware to employees
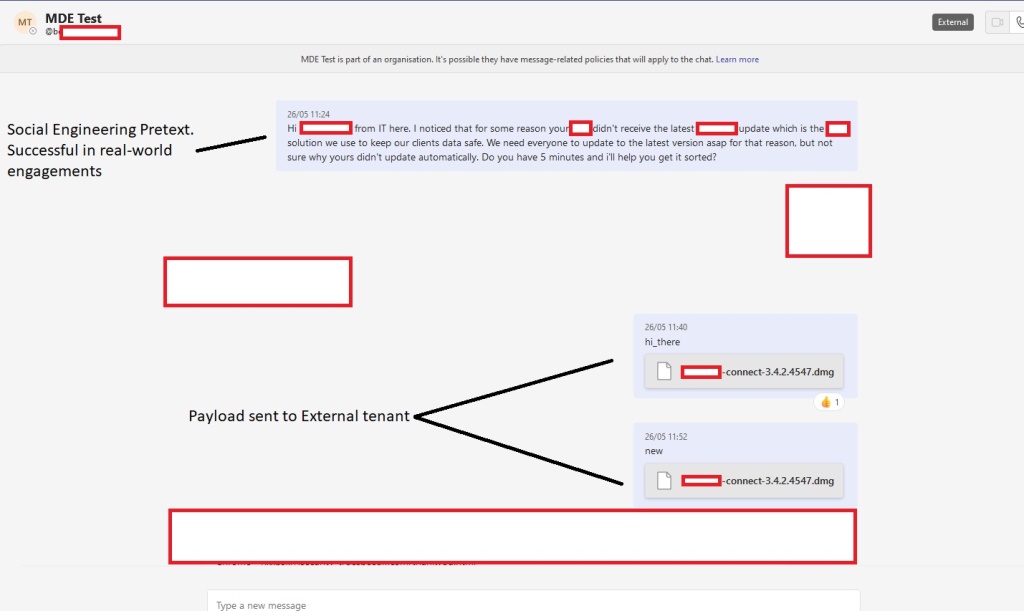
With a social engineering pretext to prime the target, the method of exploiting the vulnerability has a considerable chance of success.
Published on 26th June 2023
Security researchers have uncovered a bug that could allow attackers to deliver malware directly into employees’ Microsoft Teams inbox.
“Organisations that use Microsoft Teams inherit Microsoft’s default configuration which allows users from outside of their organisation to reach out to their staff members,” Jumpsec researcher Max Corbridge explained.
With a social engineering pretext to prime the target, a malware delivery attack exploiting this vulnerability has a considerable chance of success.
Bypassing security controls
Many organizations have permissive security controls that allow external tenants (M365 users outside the organization) to message their employees. There’s a reason for that: they may want and need to allow communications via Teams with members of other organizations, service providers, and so on.
These external users (tenants) by default can’t sent files to employees of another organization, but the client-side security controls that disallow this can be bypassed, Corbridge and fellow researcher and Jumpsec’s Head of Offensive Security Tom Ellson discovered.
“Exploitation of the vulnerability was straightforward using a traditional IDOR technique of switching the internal and external recipient ID on the POST request,” they explained.
This allows the external tenant/attacker to send a malicious payload that will appear in the target’s inbox as a file for download.
The malicious party could further increase the probability of a successful attack by registering a domain similar to the target organization’s domain, registering it with M365, and using an email address that mimics the address of a known member of the target organization.
The incoming message will be tagged with an “External” banner and the target will be warned to be extra careful when interacting with this “external” user, but a significant percentage of employees will likely ignore the warning.
“When this vulnerability is combined with social engineering via Teams it becomes very easy to start a back-and-forth conversation, jump on a call, share screens, and more,” Corbridge noted.
“When using this on a real engagement the pretext of an IT technician was used to ask the target if they could jump on a call to update some critical software. Once on the call this vulnerability was leveraged to deliver a payload and, when combined with a full social engineering attack, was implicitly trusted by the target.”
Microsoft Teams as a vehicle for malware delivery
The beauty of this tactic is that it sidesteps nearly all modern anti-phishing security controls, and particularly those related to email.
Also, while most employees have been taught not to click on links or download attachments from unsolicited emails, many still inherently trust identities in Teams and messages received via the platform – and attackers have realized that.
Corbridge says that they’ve notified Microsoft of their finding and that the company said this vulnerability “did not meet the bar for immediate servicing.”
Here’s hoping that the time for servicing will come soon. In the meantime, he advises organizations to:
- Remove the option of external tenants being able to contact employees (if not needed)
- Change the security settings to only allow communication with certain allow-listed domains (if the number of organizations they need to keep in touch is small), and/or
- Educate staff on the possibility of productivity apps such as Teams, Slack or SharePoint being used by attackers to mount social engineering attacks
Detecting attempts may prove difficult, since Microsoft currently doesn’t provide logs that cover potentially malicious events originating from external tenants, and using web proxy logs to alert on staff members accepting external message requests offers very limited insight, he added.












